Latest Version
2.3.0
February 17, 2025
Shenzhen Chenxi Information Technology Co., Ltd
Developer Tools
iOS
57.2 MB
0
Free
Report a Problem
More About Http traffic capture
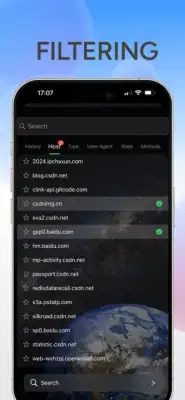
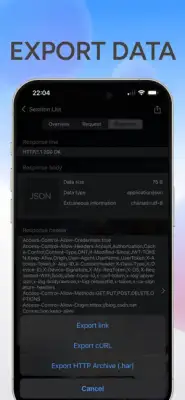
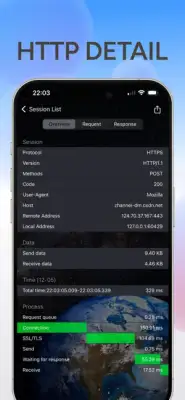
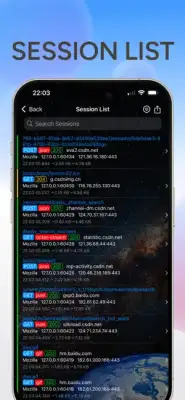
The application provides robust features for analyzing web traffic, supporting both HTTP and HTTPS protocols. One of its key functionalities is the capacity to process a variety of data types, including HTML, JavaScript, CSS, and various image formats such as webp, jpeg, and png. Furthermore, it enables users to set specific rules for packet capture, allowing for tailored data collection based on user needs. It also retains historical records of captured packets, which can be filtered based on content for easier analysis, and allows users to export this information for external use.
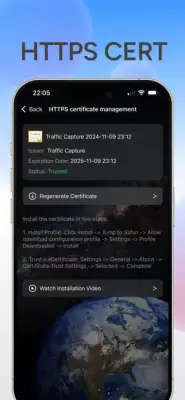
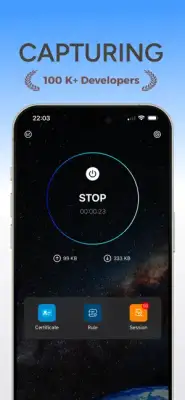
Installation and operation of the software is straightforward. It captures HTTP traffic by default, but for HTTPS analysis, users must first install a necessary certificate. When users start the packet capture, the system automatically creates a VPN connection that routes data through a local HTTP proxy server for analysis. If the VPN setup is rejected, capturing will not proceed. Users can easily manage sessions by clicking through an orange task bar interface to view request and response data, which can be exported if needed.
The software employs a unique method for analyzing data packets, particularly for HTTPS connections, requiring a trusted certificate for complete access. This means that security is a primary consideration for its design. The application generates CA keys and certificates dynamically, keeping them isolated in a secure environment to prevent unauthorized access. Each user's certificate is unique and cannot be shared, further protecting user data. Additionally, after uninstalling and reinstalling the application, the previously generated certificates become invalid, reinforcing data integrity and security protocols.
Data security is prioritized, with all captured HTTP data stored locally on the user’s device, ensuring that no information is uploaded elsewhere. The software also includes safeguards against unauthorized modifications to network requests, helping maintain proper usage. Additionally, users are informed that the certificates have a limited lifespan of one year, after which they must generate new ones. Overall, this application combines functionality with a strong emphasis on privacy and security, making it a reliable tool for traffic analysis.
Rate the App
User Reviews
Popular Apps